Cylance utilizes a unified cloud reassure where you can characterize every one of the approaches for the previously mentioned key highlights. From here you can make custom establishment bundles, which incredibly works with the product appropriation on the off chance that you have countless endpoints to secure.
Once introduced, Cylance PROTECT plays out an underlying output on all records on the PC to distinguish potential malware. In principle, this is the lone sweep required and further outputs are not performed, with the exception of when there is a huge change to Cylance AI calculations. For associations subject to explicit guidelines like PCI-DDS, which require intermittent outputs, you can empower this usefulness physically.
Since it doesn’t have to perform customary sweeps or check a malware signature information base when appropriately arranged, Cylance PROTECT devours definitely less assets than the ordinary enemy of infection programming, setting aside undeniably less effort to investigate dangers and making dissemination simpler on more established PCs with restricted limit. The Cylance similarity list incorporates Linux Red Hat/CentOS adaptations 6 and 7, Mac OS X and MacOS 10 and Windows delivers all path back to Windows XP SP3.
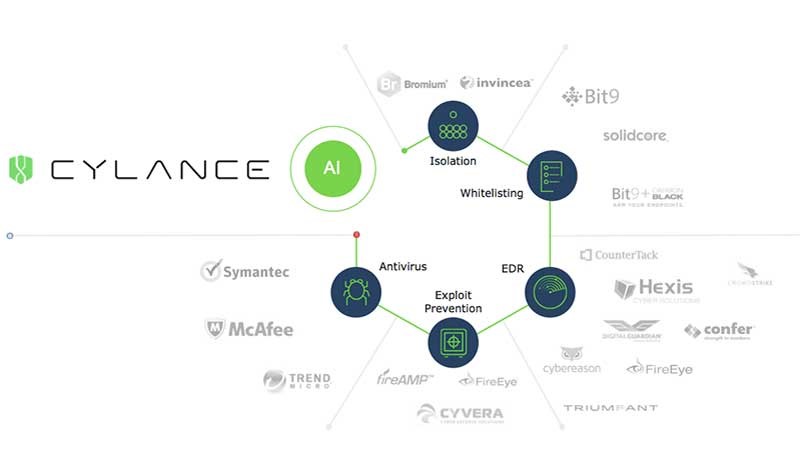
Key Highlights of Cylance Incorporates:
- Genuine zero-day avoidance
- Man-made intelligence driven malware anticipation
- Content administration
- Gadget use strategy requirement
- Memory misuse discovery and counteraction
- Application control for fixed-work gadgets
How Cylance PROTECT Works?
- Genuine Zero-Day anticipation: One of the incredible benefits of utilizing an answer that did not depend on malware marks is the chance of guaranteeing assurance against Zero-Day (obscure dangers). Since Cylance utilizes computerized reasoning models for danger avoidance, it is feasible to keep Zero-Days from being executed.
- Computer based intelligence driven malware counteraction: The most mainstream highlight of CylancePROTECT is its utilization of man-made consciousness and AI for cutting edge danger avoidance. The way that the arrangement doesn’t need to distinguish malware utilizing marks permits impeding of Zero-Day dangers, yet in addition makes the arrangement more productive in the utilization of assets like processor and memory while giving an undeniable degree of insurance.
- Content administration: Numerous dangers are dispersed through the execution of contents. CylancePROTECT permits full oversight of content execution, recognizing those that are approved and guaranteeing that no different contents are executed.
- Gadget utilization strategy implementation: Removable capacity gadgets, for example, USB sticks, compact plates or even cell phones, are a typical vector for spreading dangers. CylancePROTECT permits you to perform strategy-based administration, characterizing which gadgets can be utilized and obstructing all the other things. Straightforward as that.
- Memory abuse identification and counteraction: Fileless malware limits its exercises to the memory of the tainted gadget, as no composing is done on the PC’s circle. This kind of danger is very subtle, making it troublesome not exclusively to distinguish yet in addition restricting other security-related exercises like legal sciences. CylancePROTECT can be utilized to distinguish malignant memory utilization, for example, malware utilizing PowerShell scripts, and quickly keep the danger from being executed.
- Application control for fixed-work gadgets: At its most significant level of insurance, CylancePROTECT strategies can be set so no obscure application or executable can be run. Clearly, this methodology may not function admirably for the entirety of the association’s endpoints, yet those with a fixed job, (for example, the PCs utilized by basic framework arrangements) can profit incredibly from this sort of assurance.

Top Options in contrast to Cylance Savvy Antivirus
- Malwarebytes for Business.
- ESET Secure Progressed.
- End-client Endpoint Security.
- Webroot Business Endpoint Security.
- LogMeIn Focal.
- MVISION Endpoint Security.
- Norton Antivirus.
- Sophos Block X: Cutting edge Endpoint.
Cylance PROTECT Pricing and Cost Structure
From Cylance.com “Cylance has reclassified endpoint security. Our items and administrations anticipate and forestall, instead of responsively distinguish, the execution of cutting-edge dangers. Sent on over 14.5 million endpoints, we secure customers overall including Fortune 100 associations and governments.”
Cylance PROTECT is an endpoint security arrangement by Cylance that distinguishes, forestalls, and block dangers. With this application, IT foundations are properly ensured against various types of dangers in light of man-made brainpower that aides give more grounded security than heritage antivirus. The application examines and arranges various attributes per document and perceives at the nuclear level whether they are reliable, impartial, or something that ought to be named as a danger. Cylance Ensure valuing depends on gadgets checked.
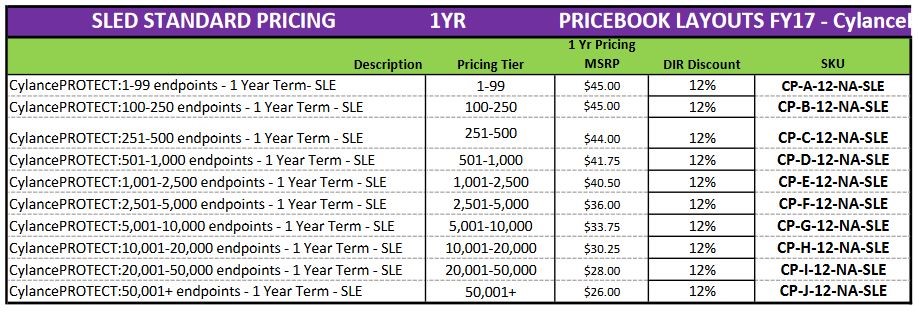
CylancePROTECT pricing:1-99 endpoints – 1 Year Term- SLE
1-99
$45.00
12%
CP-A-12-NA-SLE
CylancePROTECT pricing:100-250 endpoints – 1 Year Term – SL
E
100-250
$45.00
12%
CP-B-12-NA-SLE
CylancePROTECT pricing:251-500 endpoints – 1 Year Term – SL
E
251-500
$44.00
12%
CP-C-12-NA-SLE
CylancePROTECT pricing:501-1,000 endpoints – 1 Year Term –
SLE
501-1,000
$41.75
12%
CP-D-12-NA-SLE
CylancePROTECT pricing:1,001-2,500 endpoints – 1 Year Term
– SLE
1,001-2,500
$40.50
12%
CP-E-12-NA-SLE
CylancePROTECT price:2,501-5,000 endpoints – 1 Year Term
– SLE
2,501-5,000
$36.00
12%
CP-F-12-NA-SLE
CylancePROTECT price:5,001-10,000 endpoints – 1 Year Term
– SLE
5,001-10,000
$33.75
12%
CP-G-12-NA-SLE
CylancePROTECT price:10,001-20,000 endpoints – 1 Year Ter
m – SLE
10,001-20,000
$30.25
12%
CP-H-12-NA-SLE
CylancePROTECT price list:20,001-50,000 endpoints – 1 Year Ter
m – SLE
20,001-50,000
$28.00
12%
CP-I-12-NA-SLE
CylancePROTECT price list:50,001+ endpoints – 1 Year Term – SL
E
50,001+
$26.00
12%
CP-J-12-NA-SLE
Cylance cost based on end points is typical in the marketplace.
Pros and Cons of Cylance
Pros
- “Cylance is easy to utilize and works effectively of securing our endpoints. The conduct-based motor is considerably more exact and responsive than conventional mark-based antivirus.”
• “We have a week-by-week telephone call with the seller execution group who assists us with figuring out how to direct the item and assists us with setting up the zones and arrangements for our current circumstance.”
• “From the assessment eliminate to really moving it I have been very content with our choice to pick Cylance. I appraised all that 5 stars since I genuinely feel like they have acquired it.”
• “Cylance guarantees that every endpoint is completely secured and permits simple whitelisting for anything it gets excessively grabby with.”
Cons
- “No reports of infection disease since we utilize this.”
- “Once in a while difficult to discern whether it is working, now and again it blocks required programming and it is torment to permit it through.”
- “The program can impede important executables. While these can be whitelisted, it truly interferes with the work process to pause and need to refresh the whitelist and afterward push it to all gadgets.”
- “Can be disappointing to consistently be dealing with the whitelist.”
Closing Thoughts
Cylance PROTECT is outstanding amongst other endpoint security arrangements presently accessible on the lookout. The blend of highlights like simple dispersion and the executives, low equipment asset utilization and high danger identification/avoidance ability is without a doubt something profoundly pursued by associations wishing to be liberated from cutting edge malware.

